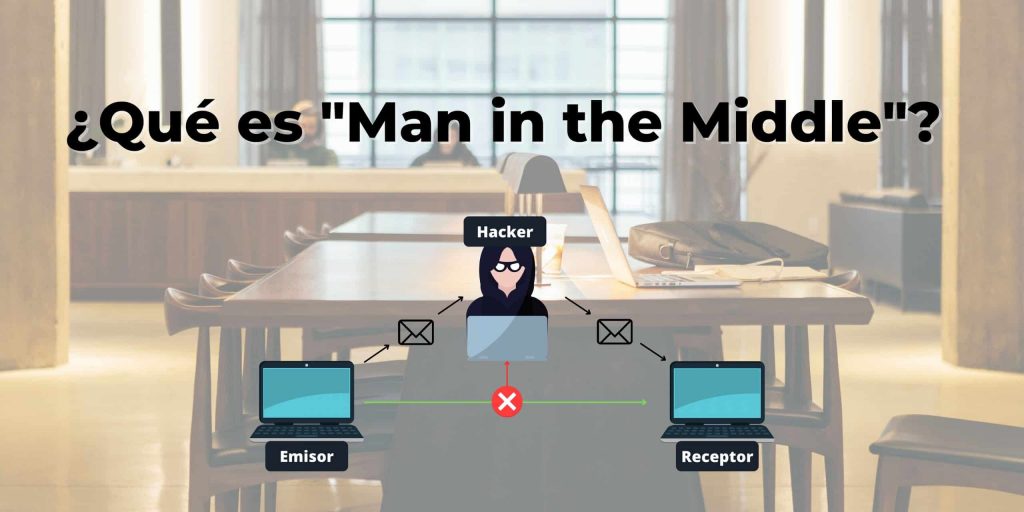
What are "Man in the Middle" attacks? As the name suggests, they are those cyberattacks in which the hacker gets in the middle of the communications between sender and receiver, intercepts the message and modifies it. Thus, some hackers managed to steal 1 million euros from an Israeli Startup, and as a consequence, bankrupt it.
The attack intercepted the communications between the venture capital and the Startup, thus managing to cancel a face-to-face meeting between the two, and modified the account number, attached to an email, for the transaction of the funds. The venture capital paid the amount into a fake account controlled by the hackers, thinking it was the Startup's. (access the full article)
How is it done?
How is it done? There are different ways to carry out the hack, but the objective is always the same. YoIntercept the message and modify it before it reaches its recipient. The message is passed through an unsecured network, controlled by the cyber attacker, and the communication is passed through a network that is under their control. For example, broadcast a Wi-Fi network with an SSID similar to that of the authorized network, and try to get broadcasters to connect to the unsecured network.
How does Tranxfer help mitigate these types of attacks?
Tranxfer offers a secure channel, which completely eliminates this cyber threat thanks to its advanced security policies. The files sent by Tranxfer travel with End-to-End encryption. This ensures that the genuine version of the file is available and that there is no one else behind the communications. At Tranxfer we want to raise awareness that cyber threats are real and much more frequent than is generally believed. It is vital to provide your organization with a computer security scheme to prevent it from becoming an easy target for cyber attackers.
So, in these cyber attacks, the hacker or cyber attacker intercepts the message when it is between the Sender and Receiver. These attacks are difficult to detect since the sender is who they say they are, and the message arrives through normal communication channels and tone. The only thing is that the hacker or cyber attacker has intercepted the message and modified it for their benefit. This cause was one of the 5 most common last year 2021. Its equivalent in the offline world would be that the postman modified the letter before delivering it to its recipient. Request one meeting with us and we will study your case